Best practices to manage permissions
This page tackles the best practices to have a smooth use of the windows built-in access control and avoid having trouble to access information either on a local PC or on DFS folders.
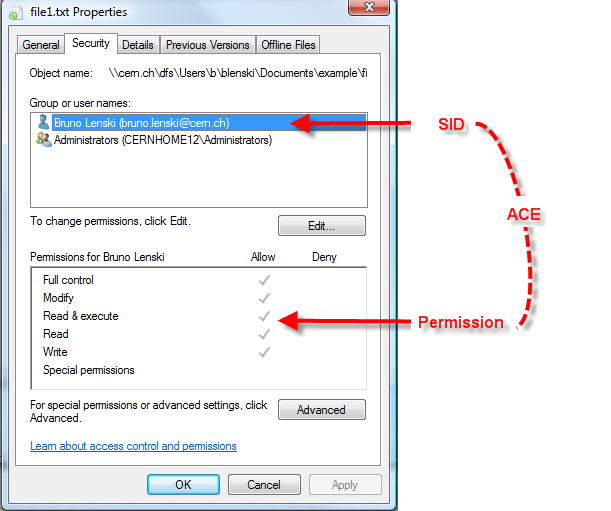
Each file/folder in windows have, within its property, a tab called Security :
This tab contains all information relative to the security of the file/folder. In the example on the left we can see that this information is composed of a SID (basically a group/user Name) and a set of permissions.
The edit button allows one to change those permissions but, what are the rules over permissions?
Rule 1 - Never remove the administrator entry.
The administrator entry is used by the system to access information on the file. If one remove the right for administrator to access the file side effect could be that backup will not be effective. Moreover, for obvious maintenance reason, the administrator of the system can always grant himself access. So not allowing administrator to access the data does not make it more secure.
Rule 2 - Do not use deny Permission.
If one does not want someone to access a folder/file, it is better to not giving him the permission to access than denying him access. This is due to the resolution method of access. As first deny are taken into consideration, if you are member of IT-IS for instance and deny access to a folder to IT-IS. Then you will be denied access even though you have also an entry in the list granting you access. For more information one can read the help pages on Managing ACL.
Rule 3 - User Groups to give access to multiple persons
If you want to grant access to person in your group to a given folder, you should use as user name to give permission. One should not add all members one by one for the following reason: Maintenance!!! If someone leave/join the group then you would have to modify permission on every file. This operation is cost full whereas adding someone to a group is a straight forward operation and is done automatically when one enter CERN for built in groups.
e-groups: http://e-groups.cern.ch
These pages allow you to create and manage your own groups
Rule 4 - Check user permission in case of doubt
While granting permission, one should want to verify if a given user/group has access to the resource he is managing. This can be done easily the windows explorer. To do this operation, one should open the security Tab of the file/folder. Then one should:
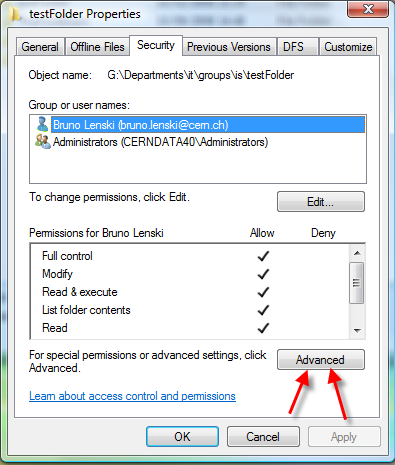
1- Click on the "Advanced" Button
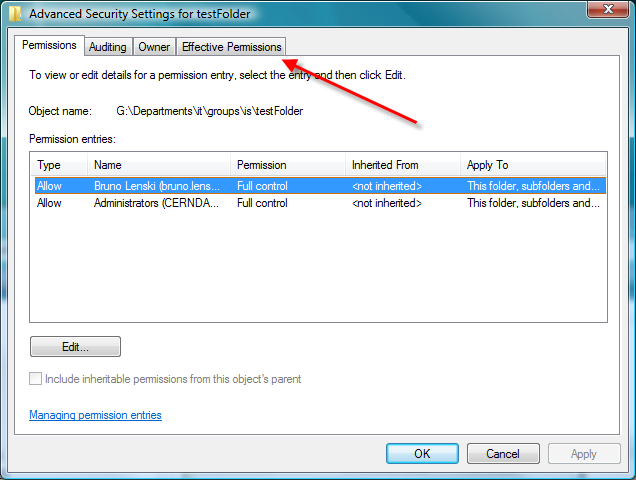
2- Open the "Effective Permission" tab
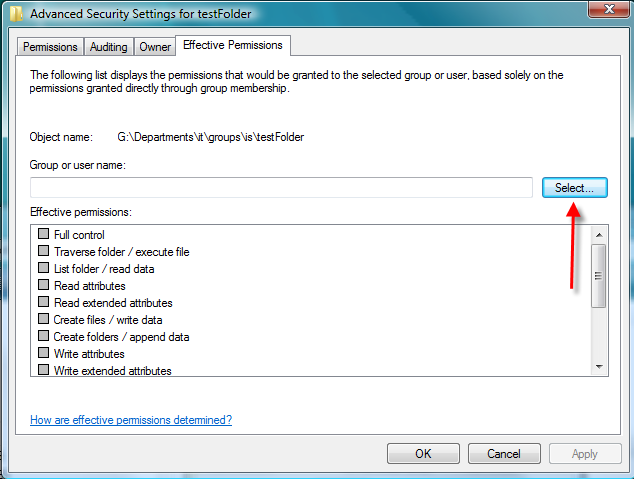
3- Click on "Select ..." to be allowed to enter a user/group name on a pop up screen
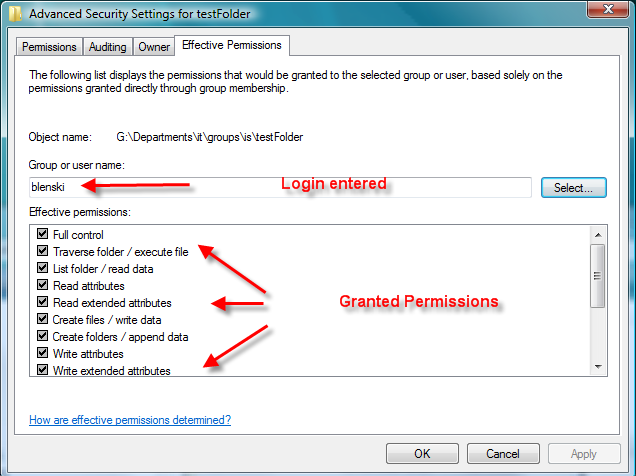
4- Click on "OK" in the pop up screen to display what permission are granted
Thus, as described Permission handling is a difficult topics but everyone should be able to handle that problematic using the 4 rules describes above.
For more information on file security, please consult the "Managing ACL" page in the help pages.