ESET Endpoint Security for Windows
If you need Help!
- About the installation of ESET, you can report an incident / submit a request.
- About infection on your device, you can report an incident / submit a request.
- You can also reach the Service Desk by phone at 77777 or by e-mail at service-desk@cern.ch.
- Visit the CERN Computer Security website.
What is ESET Endpoint Security ?
ESET Endpoint Security represents a new approach to truly integrated computer security. The most recent version of the ThreatSense® scanning engine, combined with a custom Firewall and Email client antispam module, utilizes speed and precision to keep your computer safe. The result is an intelligent system that is constantly on alert for attacks and malicious software endangering your computer.
ESET Endpoint Security is a complete security solution to combine maximum protection and a minimal system footprint. The advanced technologies, based on artificial intelligence, are capable of proactively eliminating infiltration by viruses, spyware, trojan horses, worms, adware, rootkits, and other Internet-borne attacks without hindering system performance or disrupting your computer.
It is provided for CERN users to protect their personal and professional devices, improving the security of your devices and hence CERN in general.
ESET Endpoint Security prevents malicious software from infecting your device by using:
- Antivirus and antispyware: Proactively detects and cleans more known and unknown viruses, worms, trojans and rootkits. Advanced heuristics flags even never-before-seen malware, protecting you from unknown threats and neutralizing them before they can do any harm. Web access protection and Anti-Phishing monitor communication between web browsers and remote servers (including SSL). Email client protection provides control of email communication received through the POP3(S) and IMAP(S) protocols.
- Regular Updates: Regularly updating the detection engine (previously known as "virus signature database") and program modules is the best way to ensure the maximum level of security on your computer.
- ESET LiveGrid® reputation system: ESET LiveGrid® enhances the effectiveness of ESET security solutions by leveraging a global network of endpoints to provide real-time threat intelligence and improve threat detection capabilities.
- Realtime protection: By default ESET is configured to monitor your PC all the time and will alert you when a virus, trojan, spyware or other malicous software attempts to install or run on your computer.
- Automatic scan: A full system scan is scheduled to run automatically on install, startup and during virus definition updates.
- Manual scan: You can also manually use ESET to scan your entire PC or specific drives, files or folders for potential threats that might put your device at risk.
- Firewall: Connections to your device are audited and automatically allowed or denied based on their reputation. You can customise these rules to ensure maximum security without disturbing access to websites that are important to you.
- Windows Update Monitoring: Alerts you if your computer is missing key updates that address security concerns.
The original ESET documentation can be found here. More information about the technologies that are used from ESET can be found here.
How to install ESET Endpoint Security ?
ESET Endpoint Security is available from the CERN App Store for your personal/self-managed Windows devices and will be gradually rolled out to all CERN centrally managed Windows devices through CMF. CERN centrally managed Windows devices can manually install ESET Endpoint Security through the package ESET Endpoint Security (only PROTECT) of the NSC Default NICE
Warning
- To avoid performance impact, we recommend users to manually uninstall any other anti-virus programs they may have before installing ESET Endpoint Security from CERN AppStore.
How to open ESET Endpoint Security?
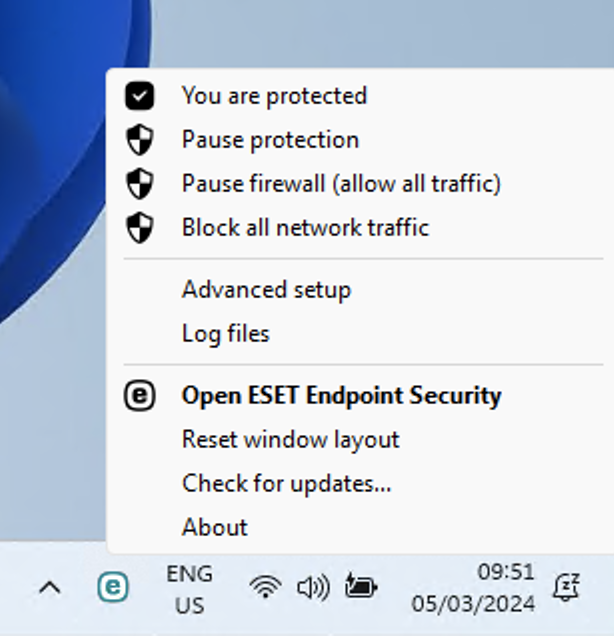
Click the ESET icon in the notifications tray (at the bottom right) of your Windows screen.
If you right-click ESET icon in the notification tray (at the bottom right) of your Windows screen, you will get a context menu with valious options related to the ESET Endpoint Security software installed on your system.
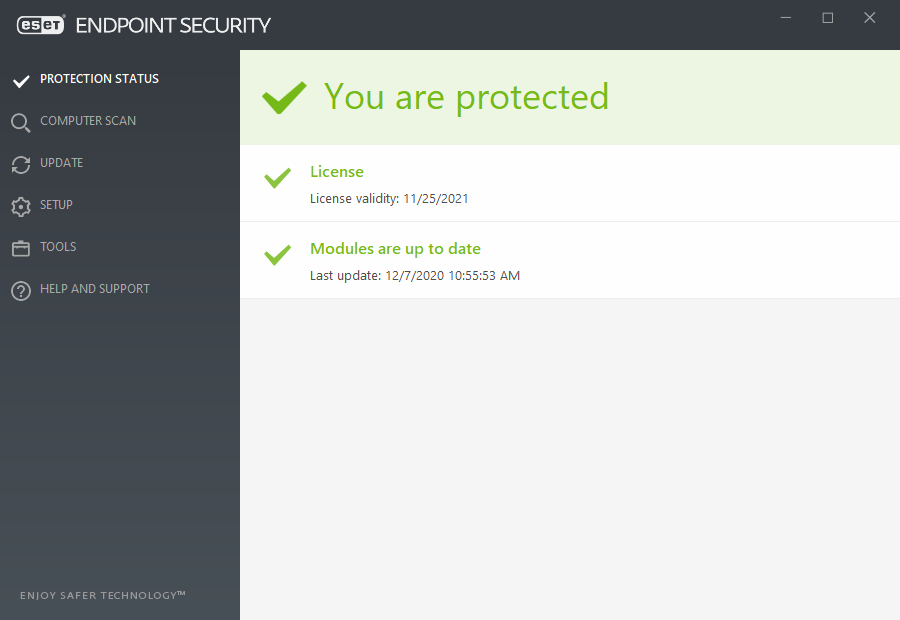
The user interface of ESET offers the following features (see below).
| Features | Functionnality |
|---|---|
| Protection status | Provides information about the protection status of ESET |
| Computer scan | This option allows you to configure and launch of Smart scan, Custom scan, or Removable media scan. |
| Update | Displays information about the ESET Endpoint Security, it's modules and allows to check for updates manually or Change update frequency. |
| Setup | Select this option to adjust your Computer, Network and Web & email security settings. |
| Tools | Provides access to Log files, Running processes, Security report, Secure Browser, System inspector, Scheduler and Quarantine. |
| Help and support | Provides details about the license, access to help files, ESET KB and ESET Technical Support. |
More details can be found here.
How to perform a manual scan ?
ESET uses Real-Time (RT) protection to intercept viruses and other malicious files on your computer without actively scanning the entire system disk. RT protection scans files when they are created, opened or executed and deletes them if they are malicious.
You can manually run a scan of specific files or your entire computer on demand. We recommwnd that you perform regular (for example once per month) in-depth scans of your system to detect viruses not detected by Real-Time file system protection. This can happen if Real-time file system protection was disabled at the time, if the detection engine was obsolete or if the file was not detected as a virus when it was saved to the disk.
This is only necessary when you suspect your computer has been compromised/infected or requested by the CERN Computer Security Team.
ESET offers 4 scan options
- File Scan - Scan individual files for threats.
- Scan your computer - Scans all local disks and cleans threats.
- Custom scan - Select the scan targets, cleaning level and other parameters.
- Removable media scan - Scanning of USB, DVD, CD and other removable media.
- Repeat last scan - Quickly launch the previously performed scan using the same settings as before.
File scan There are 3 ways to initiate a file scan:
-
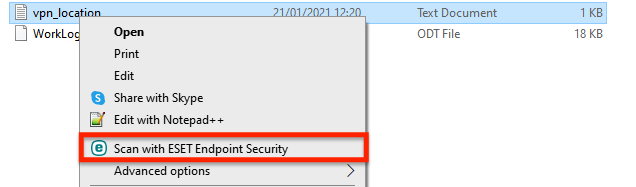
Directly via Windows Context Menu a. Right click the file and select Scan with ESET Endpoint Security
-
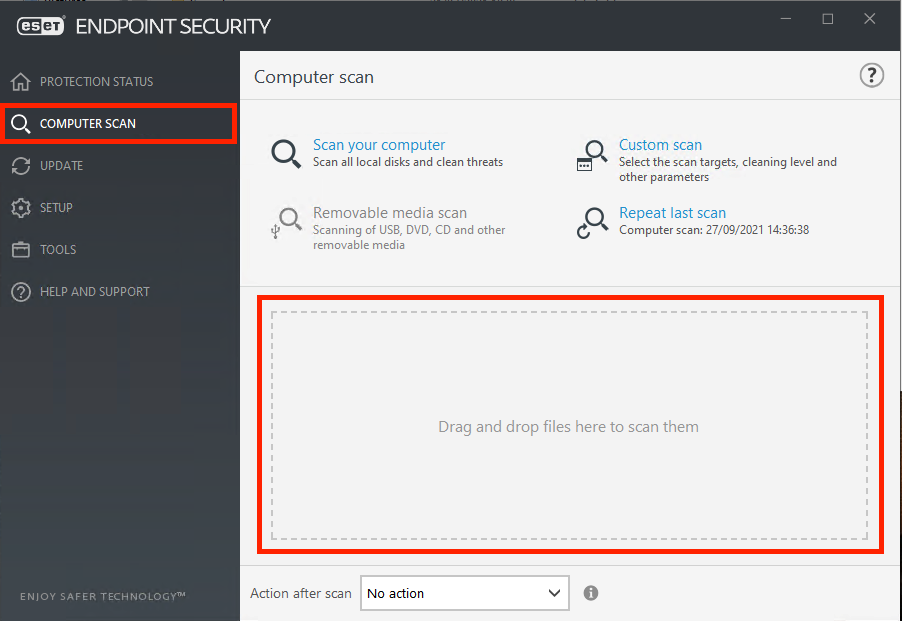
Drag and drop a file into the ESET Endpoint Security GUI a. Open the GUI and navigate to Computer Scan b. Drag the file into the area that appears labelled: "Drag and drop files here to scan them"
-
Select the file via the ESET Endpoint Security GUI a. Open the ESET Endpoint Security GUI using the procedure written above b. Select Computer Scan from the left sidebar. c. Navigate to the file/folder you want to scan or specify the full path
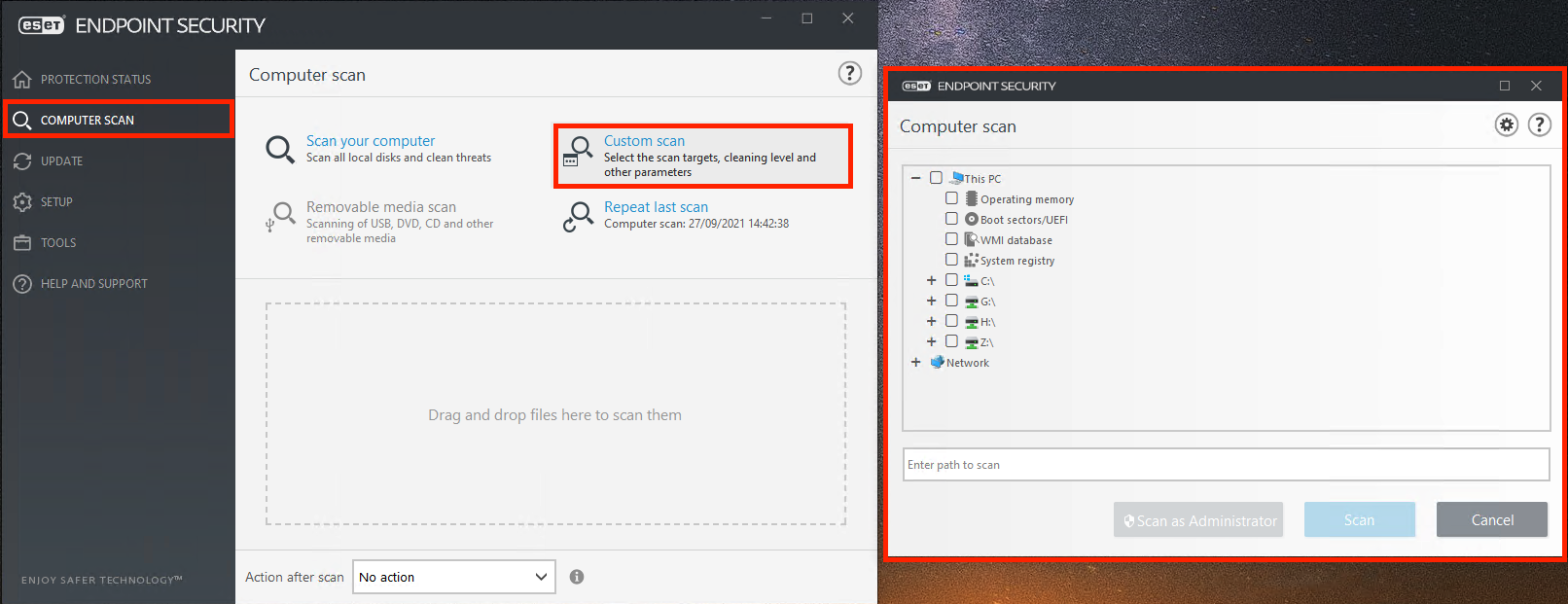
More details can be found here.
How to keep ESET Endpoint Security client & virus definitions up to date?
Updating ESET Endpoint Security can be performed either manually or automatically. To trigger the update, click Update in the main program window and then click Check for updates.
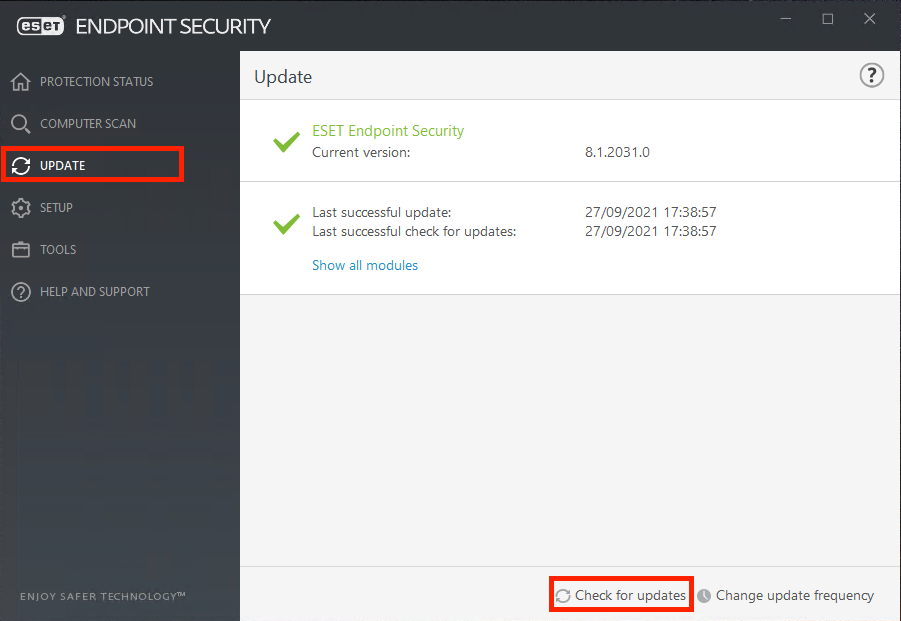
The default installation settings create an automatic update task which is performed on an hourly basis. Here you can also change the update frequency. Alternatively, navigate to Tools > Scheduler.
More information can be found here and here.
How to schedule common tasks ?
The Scheduler manages and launches scheduled tasks with predefined configuration and properties.
The Scheduler can be accessed from the ESET Endpoint Security main program window by clicking Tools > Scheduler. The Scheduler contains a list of all scheduled tasks and configuration properties such as the predefined date, time, and scanning profile used.
The Scheduler serves to schedule the following tasks: detection engine update, scanning task, system startup file check and log maintenance. You can add or delete tasks directly from the main Scheduler window (click Add task or Delete at the bottom). Right click anywhere in the Scheduler window to perform the following actions: display detailed information, perform the task immediately, add a new task, and delete an existing task. Use the check boxes at the beginning of each entry to activate/deactivate the tasks.
By default, the following scheduled tasks are displayed in Scheduler:
-
Log maintenance
-
Regular automatic update
-
Automatic update after dial-up connection
-
Automatic update after user logon
-
Automatic startup file check (after user logon)
-
Automatic startup file check (after successful module update)
To edit the configuration of an existing scheduled task (both default and user-defined), right-click the task and click Edit... or select the task you wish to modify and click the Edit button.
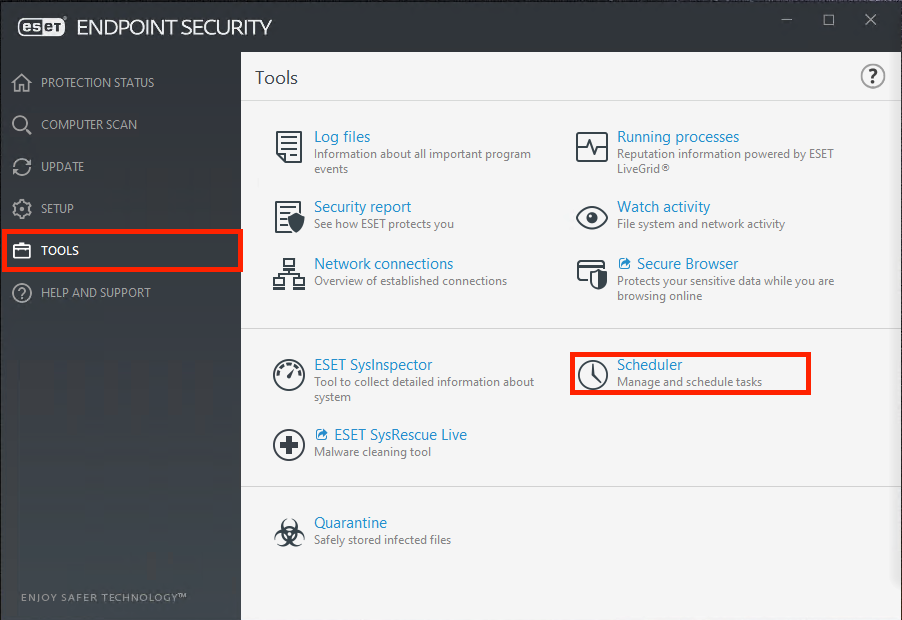
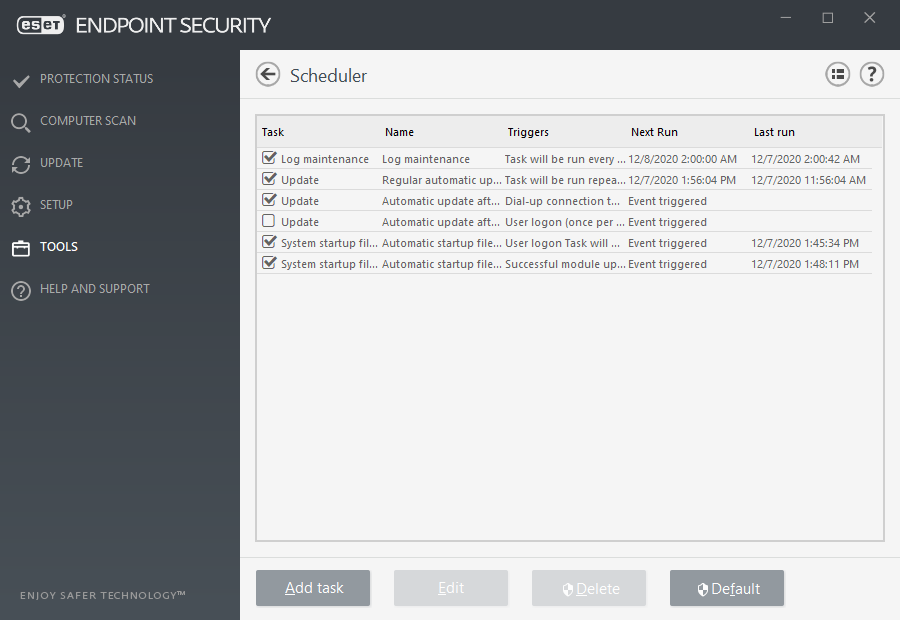
More details can be found here.
Firewall
The Firewall controls all network traffic to and from the system. This is accomplished by allowing or denying individual network connections based on specified filtering rules. It provides protection against attacks from remote computers and can block potentially threatening services.
How to allow communication for a certain application through the firewall ?
If you install ESET Endpoint Security while being connected to the machine via Remote Desktop Connection, the firewall is by default disabled after installation from CERN AppStore to prevent a network malfunction. You will prompted with the following message right after you finish your installation. Please press the button "Enable firewall" to be protected against network threats.
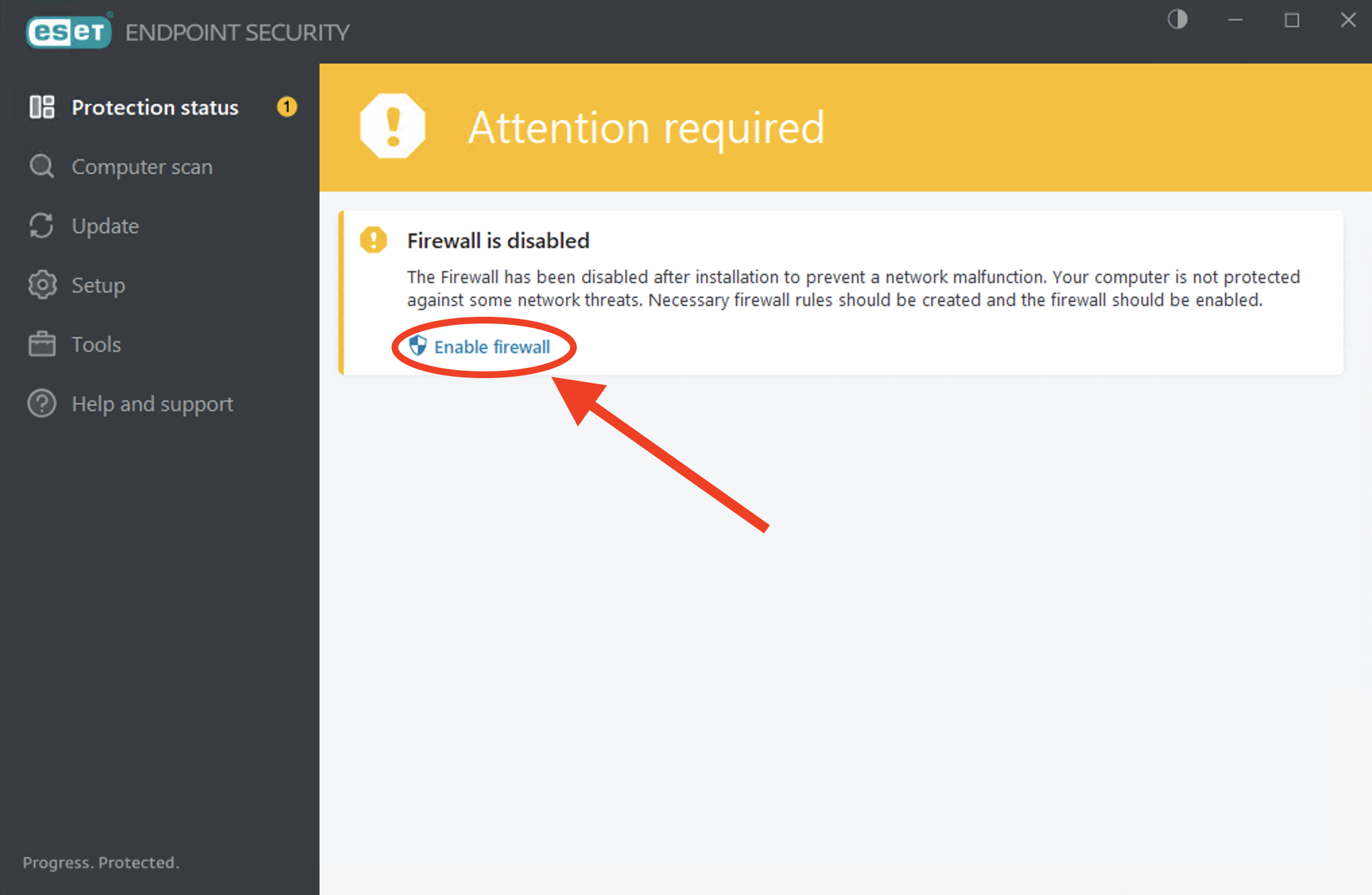
After this firewall will be in automatic mode, thereby deciding itself which connections should be blocked and allowed. This works in most cases without user intervention but sometimes it is necessary to add an exception if, for instance, a user-installed program cannot access the internet. If you find that you are having problems, you can check in the client whether ESET Endpoint Security is blocking the connection and decide whether to create an exception for it in the future. Make sure that you trust the IP address/application/port before doing so.
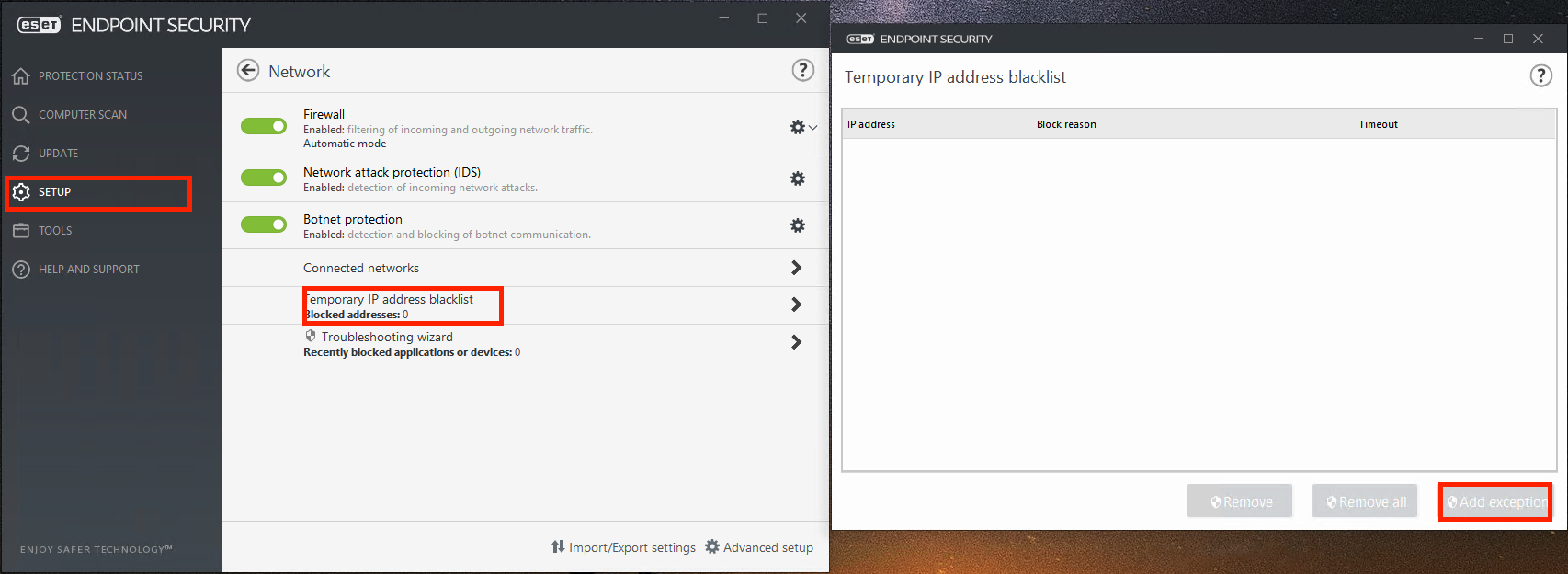
More general details can be found on the firewall here, and how to allow a connection here.
How to interpret the Protection status icon ?
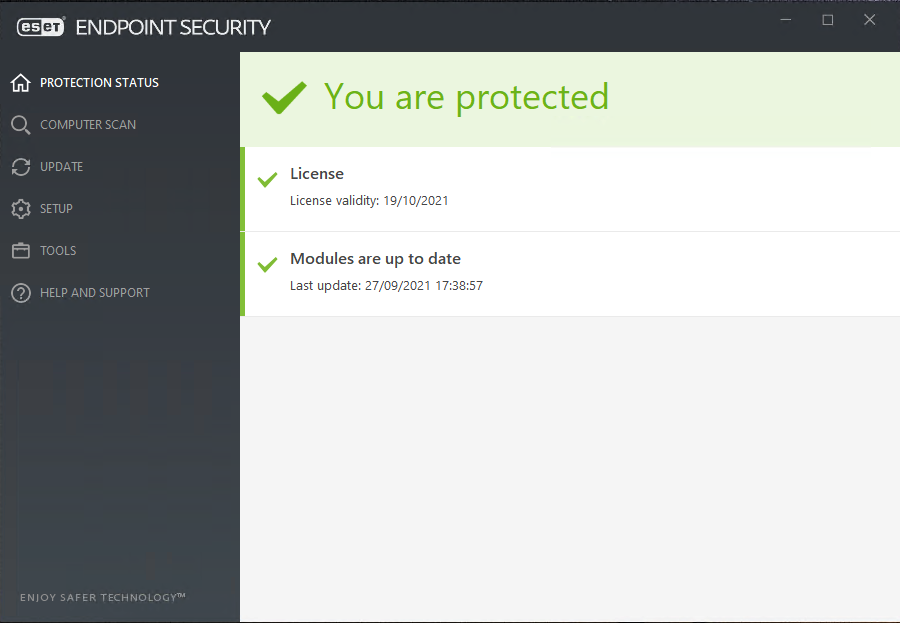
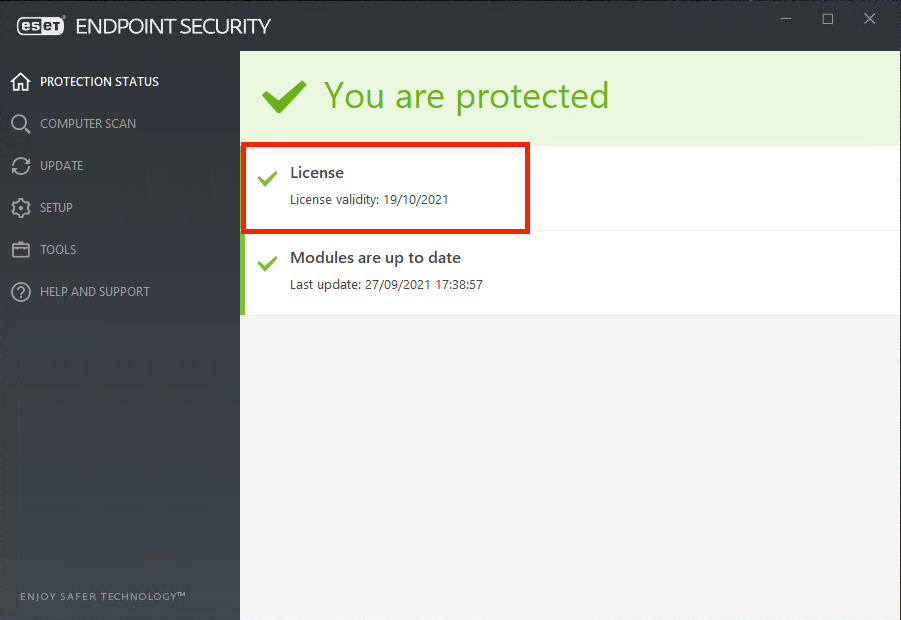
The Protection status screen informs you about the security and current protection level of your computer:
- The green Maximum protection status indicates that maximum protection is ensured (see picture below).
- A red exclamation point notification icon is displayed if a module needs attention.
- The red exclamation point (!) icon indicates that maximum protection of your computer is not ensured. You may encounter this type of notification in the following scenarios:
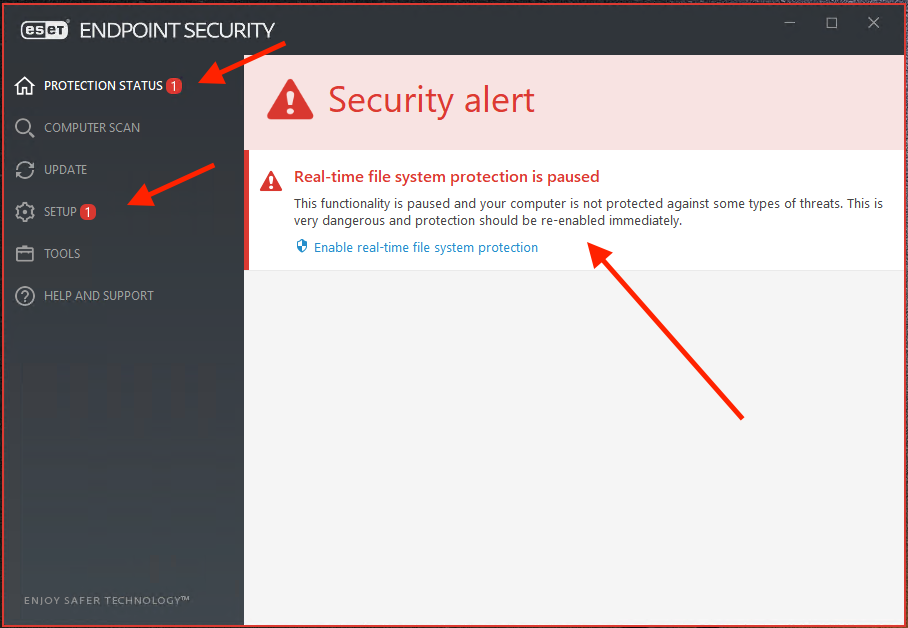
- Real-time file system protection is paused – Real-time protection was disabled by the user. Your computer is not protected against threats. Click the link Enable Real-time file protection to re-enable this functionality (see picture above).
- Antivirus and antispyware protection is paused – Click Start all antivirus and antispyware protection modules to re-enable antivirus and antispyware protection in Protection status pane or Enable Antivirus and antispyware protection in Setup pane.
- Antivirus protection is non-functional – Virus scanner initialization failed. Most ESET Endpoint Antivirus modules will not function properly.
- Detection engine is out of date – This error will appear after several unsuccessful attempts to update the detection engine. We recommend that you check the update settings. The most common reason for this error is an incorrect configured connection settings.
- Product is not activated or License expired – This is indicated by a red protection status icon. The program is not able to update after your license expires.
More details can be found here.
License Validity
For CERN devices that are centrally managed via CMF the licensing will be handled automatically. For personal or self-managed devices, the license now needs to be renewed every three years. However, this may vary depending on the contract with the vendor. This information is subject to change and will be updated accordingly. This is accomplished by re-installing or upgrading the application from the CERN AppStore. You will receive communications when action is required from you to prevent the license from expiring and thus losing protection.
What are common symptoms of an infection ?
Not all computer performance problems are caused by malicious software.
The presence of malware on your computer may not always be immediately obvious, so it is important to run regular scans. However, some of the more common symptoms are listed below:
- New toolbars, links or favourites that you did not intentionally add to your web browser.
- You type the address for a specific site, such as a search engine, but you are taken to a different website without notice.
- Your Home Page or Search Program changes unexpectedly.
- Your files are automatically deleted from your computer.
- Your computer is turned on Botnet by attackers and it is used to attack other computers.
- Unattended pop-up ads are displayed without your consent, even if you are not on the Internet.
- Onscreen Warnings about system infection from a source other than your antivirus software.
- Your PC suddenly starts running more slowly than usual.
- The ESET Endpoint Security icon disappears from the menu bar (at the bottom right) or cannot be started.